TxSSC
School Behavioral Threat Assessment Toolkit
5.0 Guiding Principles of Threat Assessment
Several key principles guide the threat assessment and management process:
Targeted violence is the result of an understandable, and usually discernible, process of thinking and behavior.
Individuals who commit targeted violence rarely “just snap.” Instead, they typically engage in a progression of thoughts and behaviors that escalated over days, weeks, months, or even years. This progression is commonly referred to as the “Pathway to Violence,” which will be discussed in the next section.Targeted violence stems from an interaction among the Subject(s), Target(s), Environment, and Precipitating Events (STEP).
Identifying, assessing, and managing potential acts of violence or other harm requires a comprehensive and holistic understanding of the situation across four interrelated domains. The team considers how each domain, and their interaction, may influence risk and guide appropriate interventions:S – Subject:
Is the subject engaging in behaviors that may pose a threat of violence or harm to self or others, cause significant disruption, or otherwise indicate a need for assistance or intervention? This includes how the individual perceives and copes with stressors, as well as the level of effort directed toward planning or preparing for violence.T – Target:
Are potential targets or others vulnerable to harm, in need of protective actions, impacted by the situation, or otherwise requiring support or intervention? Consider the subject’s access to the target and any factors that may decrease or increase vulnerability.E – Environment:
Are there environmental or systemic factors that may be contributing to or influencing the situation? This includes elements of the school climate, peer dynamics, supervision practices, classroom or campus culture, workload or academic pressures, policy implementation, or other conditions that may increase stress, enable concerning behavior, or fail to discourage escalation.P – Precipitating Events:
Are there reasonably foreseeable stressors or triggering events—such as disciplinary actions, personal losses, bullying, major transitions, or threat assessment interventions—that may escalate or de-escalate the situation?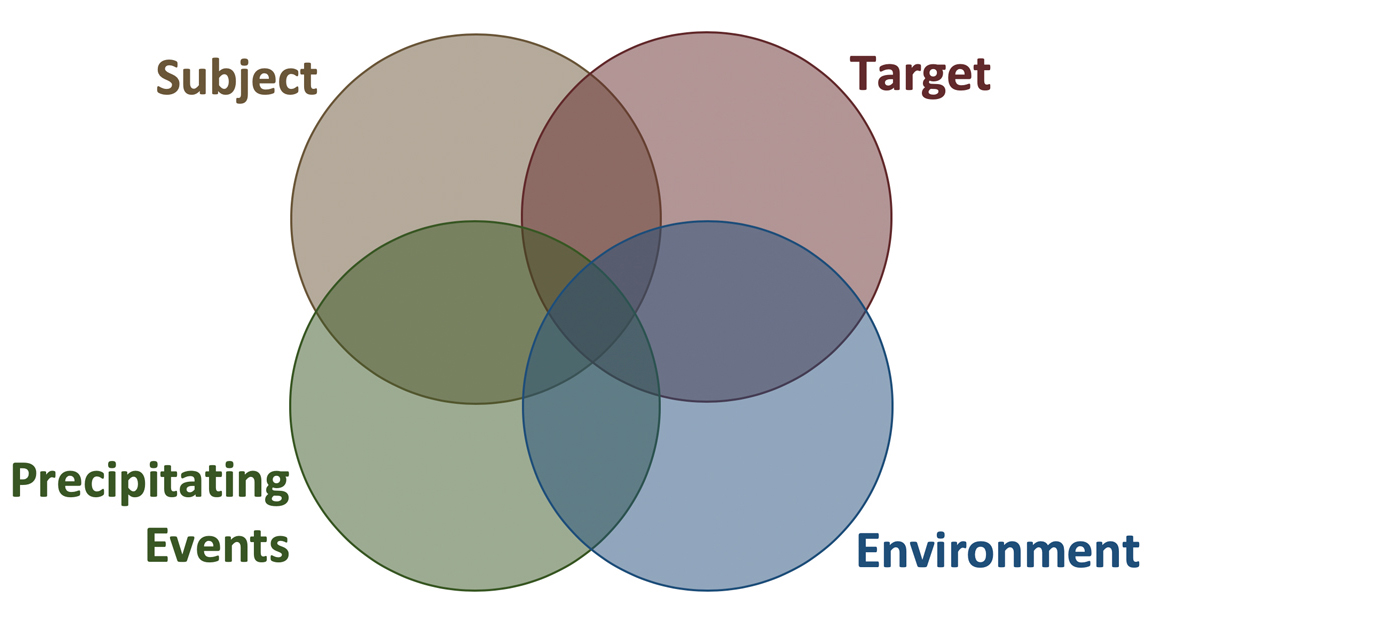
Violence is a dynamic process.
No one is either always dangerous or never dangerous. The level of concern depends on the totality of the situation. An assessment is only as good as the quality of information on which it was based at the time that it was made.An inquisitive, objective, and diligent mindset is critical to successful threat assessment and management.
Threat assessment team members must approach each case with a careful and investigative mindset — remaining thorough, accurate, fair, and persistent in gathering information. Throughout the assessment process, the team should work to collect relevant data, verify its accuracy, and understand how each piece fits into the broader context of the situation (collect and connect the dots). A key hallmark of a sound investigative process is corroboration or fact-checking — confirming information through multiple sources whenever possible to ensure a comprehensive and reliable understanding of the case.Threat assessment is about prevention, not prediction.
The team is not trying to predict whether a subject is a “violent person.” Instead, the team is trying to develop a comprehensive perspective of the situation to help prevent violence and assist those in need, even if they were never going to be violent.Effective assessment is based upon observations of behavior rather than on general characteristics, traits, or profiles.
Perpetrator profiles do not provide a reliable basis for making judgments of the threat posed by a particular individual. The threat assessment process examines the behavior of the subject in relation to the context, issues, challenges, and resources involved. This provides for an individualized, holistic, and contextually based understanding of and response to the situation.Social media and online activity are critical considerations in many cases.
Use of social media and web-based communications are commonplace in today’s society. Subjects of concern, and those who may be worried about them, often use online platforms to share their thoughts or express concerns. For individuals who may pose a threat, expressions of grievances, violent intent, planning, and preparation can often be observed through their online activities.The central question in a threat assessment inquiry is whether a subject poses a threat (i.e., is building the capability to cause harm), not just whether the subject has made a threat (directly expressed intent to harm).
Research on serious targeted violence in schools and workplaces has found that few perpetrators directly communicated a threat to their target before the violence, particularly when no prior relationship existed between them. Instead, in many incidents, perpetrators communicated their intentions or plans to others before acting. This indirect expression, often referred to as “leakage,” involves sharing, thoughts, plans, or intent to cause harm with third parties rather than the target.Importantly, individuals who ultimately pose a threat (i.e., developed the capacity and engaged in violence) do not issue direct threats to their targets. Therefore, the absence of a directly communicated threat should not lead a team to conclude that a subject does not pose a danger to self or others.
The relationship between mental illness and violence is complex.
While the presence of a serious mental illness may contribute to an elevated general risk of violence, it is far from the major factor it is often assumed to be and is rarely the sole or primary explanation for a violent act. Other risk factors have stronger overall correlations with violence.For threat assessors, the specific symptoms, behaviors, and functional impact of a subject’s mental illness, rather than the diagnosis itself, are the factors most relevant to understanding and managing a case.
A collaborative and coordinated approach between systems within the school and the community is critical for an effective threat assessment and management process.
Effective working relationships and collaborations with services and programs, both within the school (e.g., school-based mental health professionals, administrators, disciplinary officers, human resources), and in the broader community (e.g., mental health, juvenile justice, child welfare, law enforcement), are essential for identifying, assessing, and managing individuals who may be on a path toward committing an act of targeted violence.
References
Virginia Department of Criminal Justice Services. (2025). Threat Assessment and Management in Virginia Public Schools: Model Policies, Procedures, and Guidelines. Sixth Edition. https://www.dcjs.virginia.gov/sites/dcjs.virginia.gov/files/law-enforcement/files/vcscs/K-12_Threat_Assessment_Management_2025.pdf
U.S. Department of Education. (2004). Threat Assessment in Schools: A Guide to Managing Threatening Situations and Creating Safe School Climates. https://www.ed.gov/sites/ed/files/admins/lead/safety/threatassessmentguide.pdf